Revoke Access to a Device
If you enable local Encryption on a Policy, every device that uses that Policy is given an encryption certificate. When a user logs on to a device, they can only access the encrypted data if the certificate is in place.
If a device goes missing or is stolen, you can use Endpoint Cloud to remotely remove the certificate from the device. Once the certificate is removed, anyone including the logged-on user will be unable to access the encrypted data on the device (as the certificate is not on the device).
Using Endpoint Cloud to remove a certificate is known as "revoking a device".
To revoke a device:
- Click Inventory or Protection.
- In the devices list, click on the device you want to revoke. The device's slide-in panel appears.
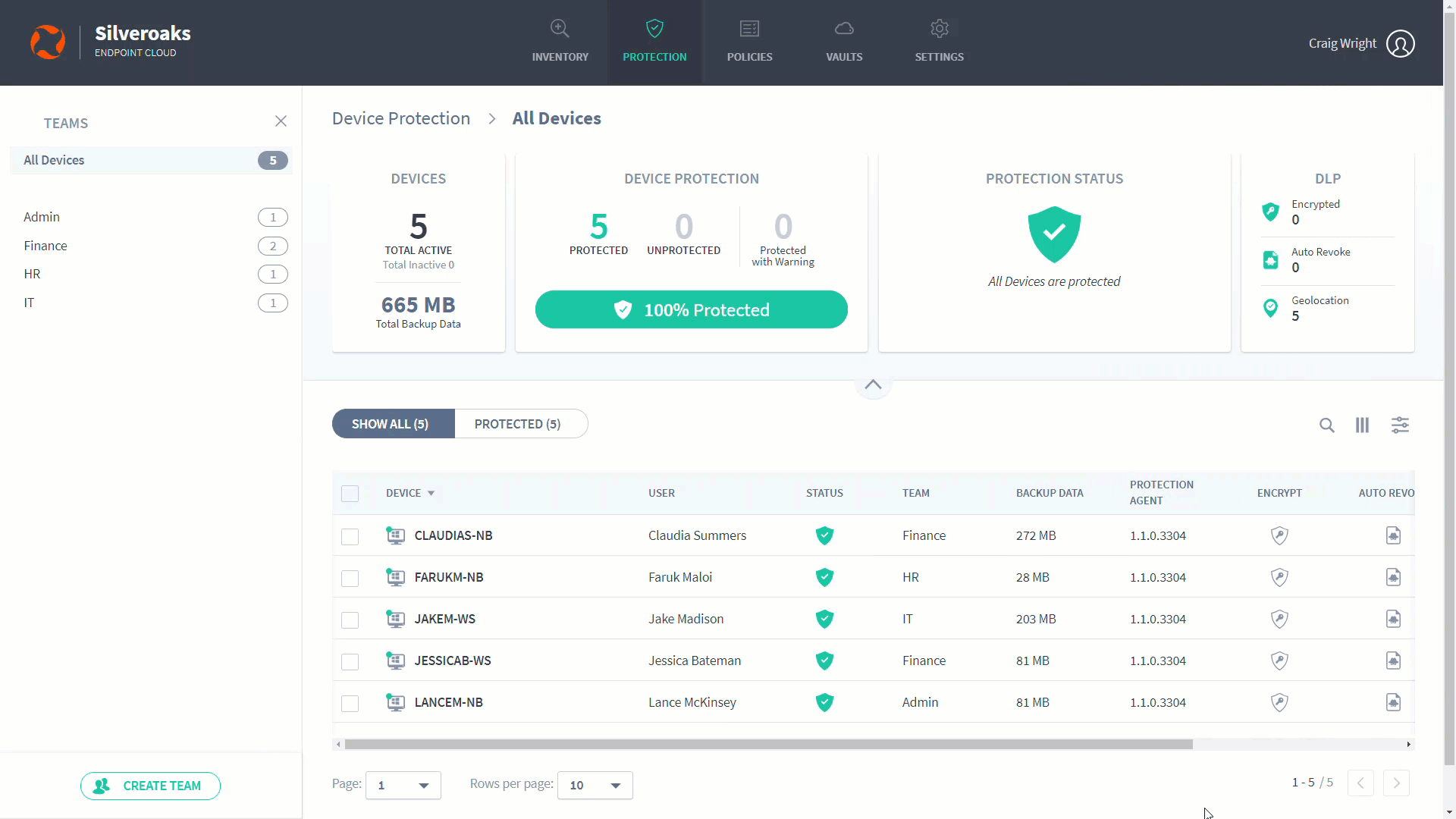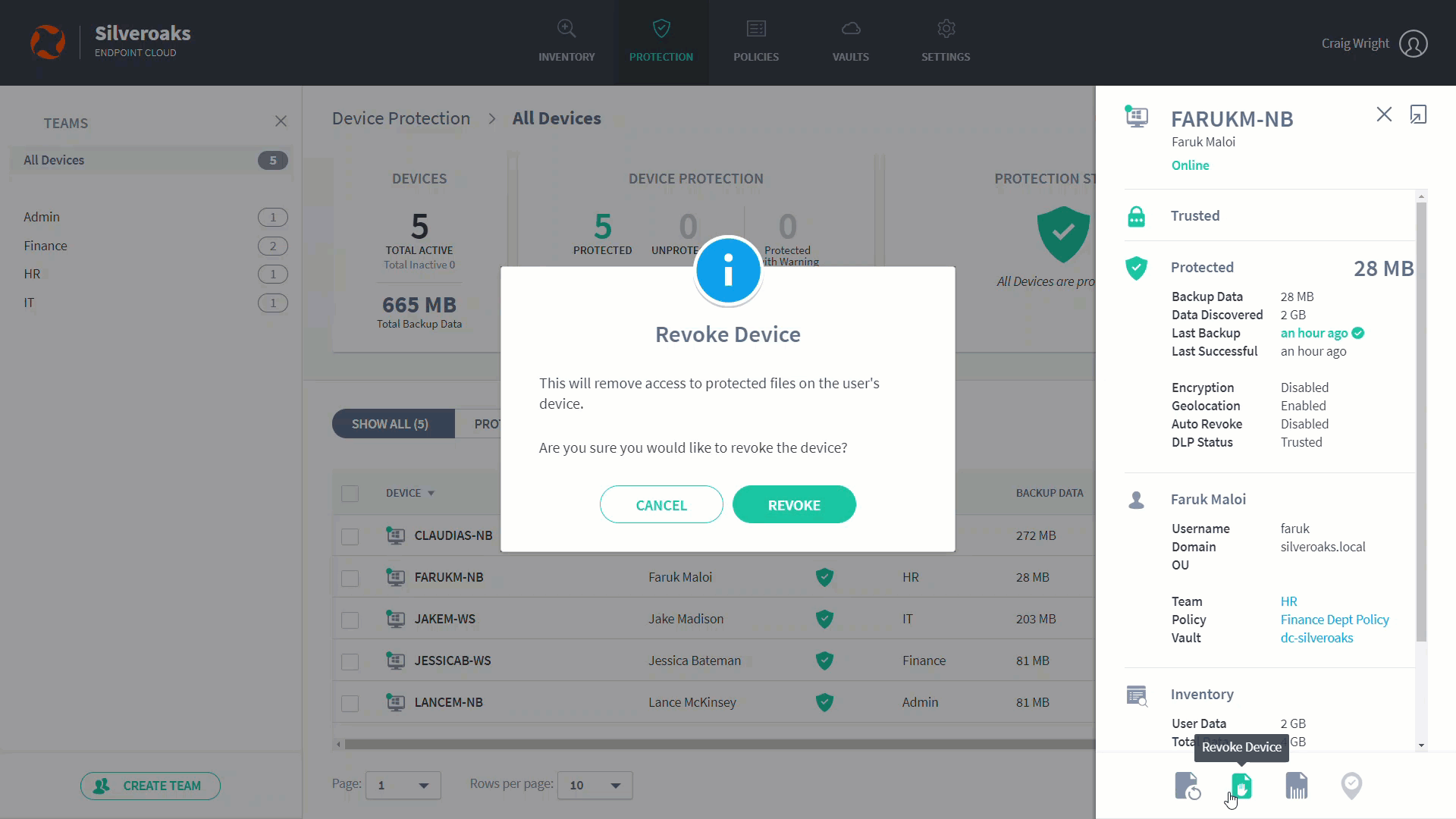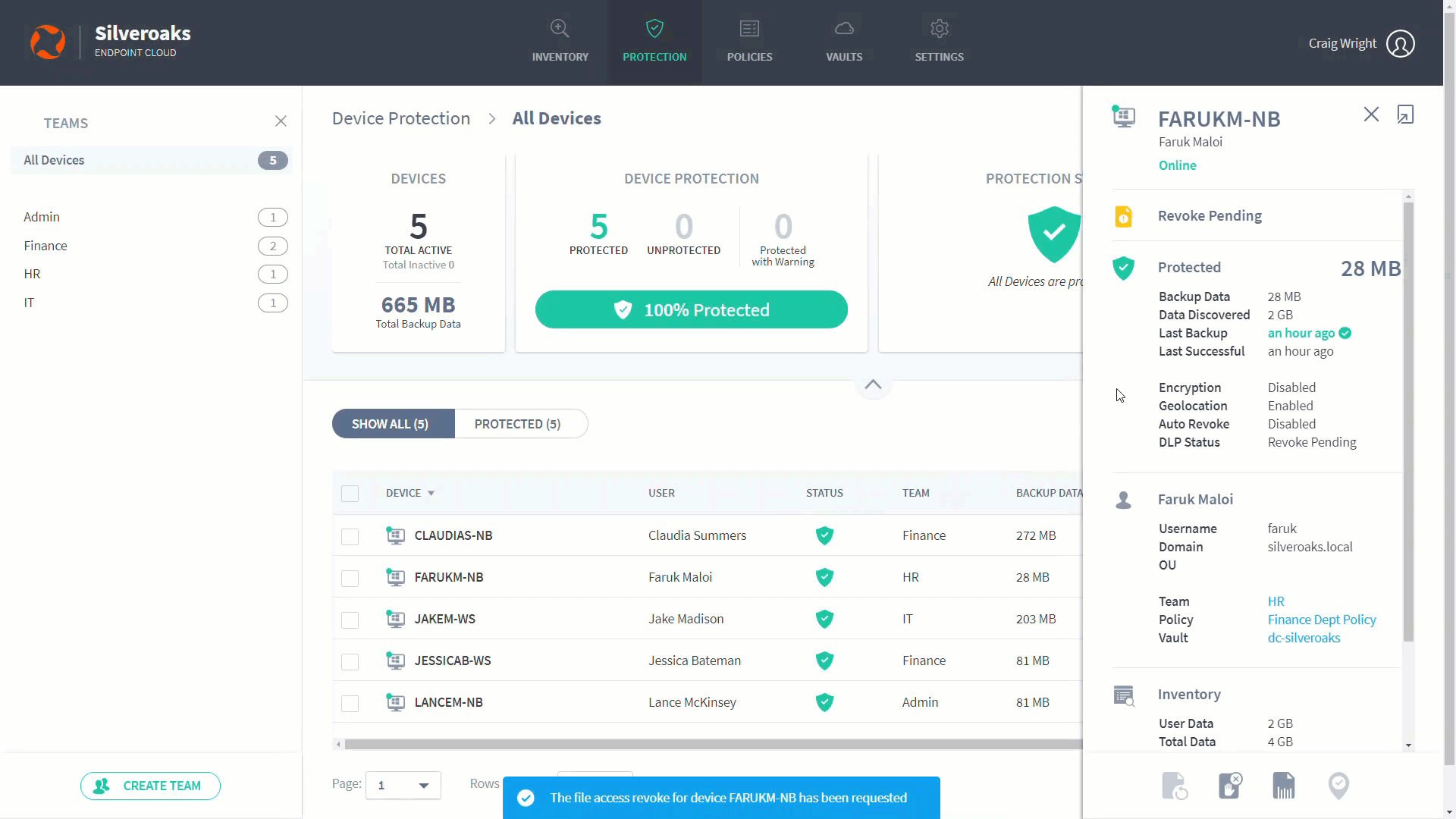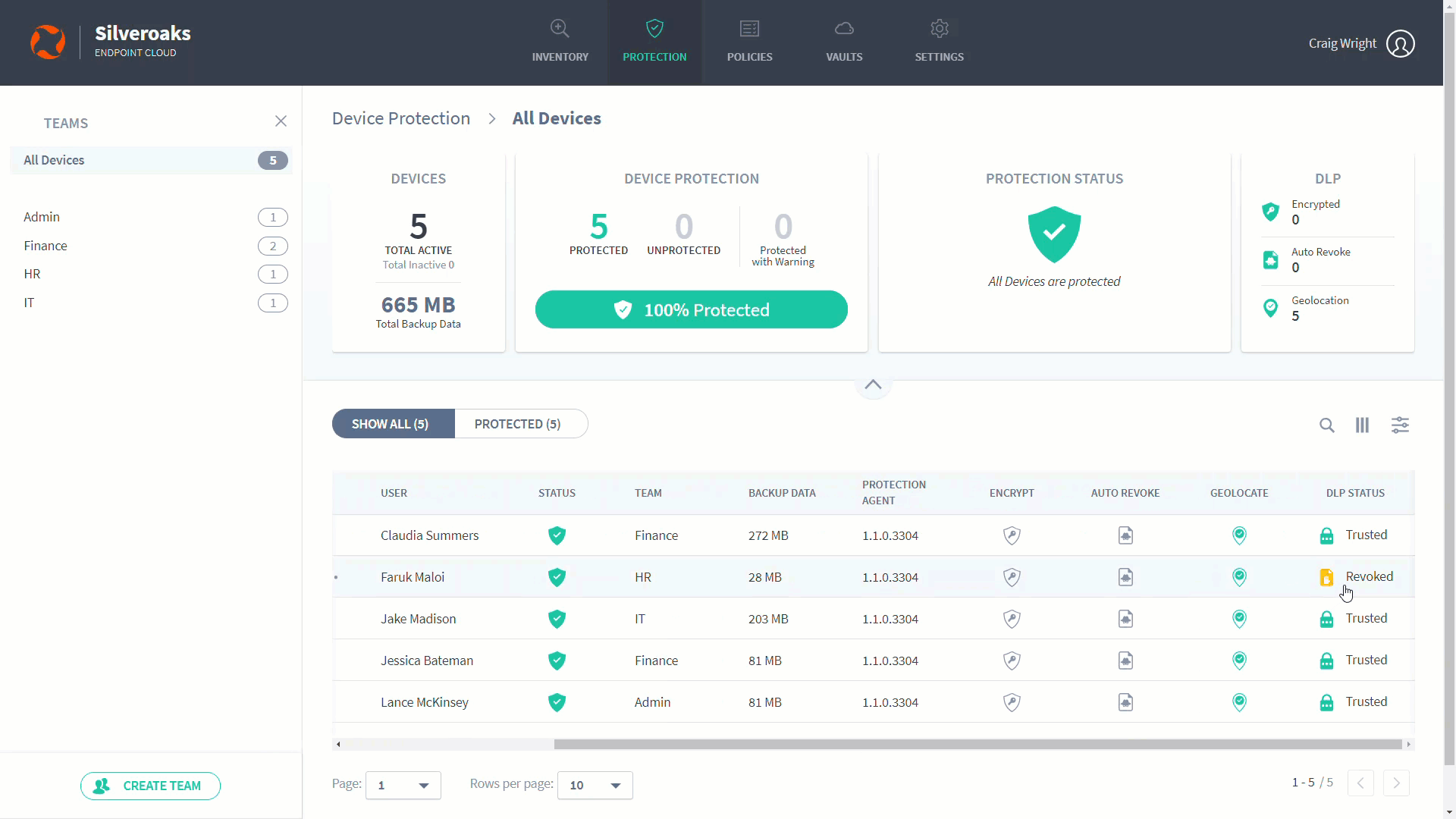
- Click on the Revoke Device icon.
 Note
NoteThe Revoke Device icon is also available on the Device profile page (from the Inventory or Protection page, display the device's side panel, then click the view details icon to display the Device profile page).
- Click Revoke to confirm. The request to revoke the device is made. You can cancel the revoke request if required (display the device's slide-in panel or device page, and then click the Cancel Revoke icon).
If Auto Revoke is enabled on a Policy, Endpoint Cloud will automatically revoke the certificate of any protected device that does not connect to Endpoint Cloud within a 30 day period. (You can change the auto revoke time period in the Policy settings).